

Introduction
DomainKeys Identified Mail (DKIM) is a protocol that contributes to DMARC compliance and requests the sender origin to take responsibility for sent messages that can be verified by mailbox providers. Essentially, it enables the outbound domain to digitally sign email to provide legitimacy for the recipient. Together with SPF, DKIM will significantly increase email delivery rates. It is not hard to implement DKIM on your own. At the end of this tutorial, we should achieve both SPF and DKIM Passes when we check ‘Show original’ of an email sent to our Gmail.

Prerequisites
To follow along with this tutorial, you will need the following:
- Email hosting provider (e.g. Zoho, Google and MXroute)
- DNS management (e.g. cPanel, DirectAdmin and CloudFlare)
- Knowing where to find MX, DKIM and SPF records associated with your email provider.
Step 1 – Add DKIM (TXT) Record
We will use MXroute as our email hosting provider for this tutorial. After adding a new domain in the admin panel, a bunch of records will be auto generated at the DNS Management page. The only DNS record we will use from this page is the DKIM key. Find a record that has a bunch of text starting with “v=DKIM1; k=rsa; …“
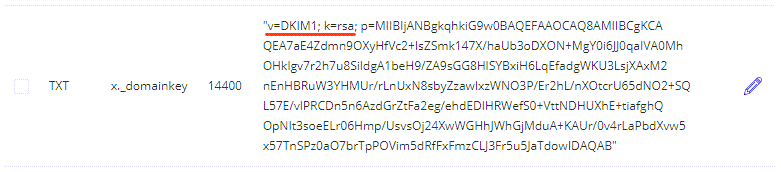

That is what we need to copy to our clipboard, to add as TXT record at CloudFlare DNS Management.
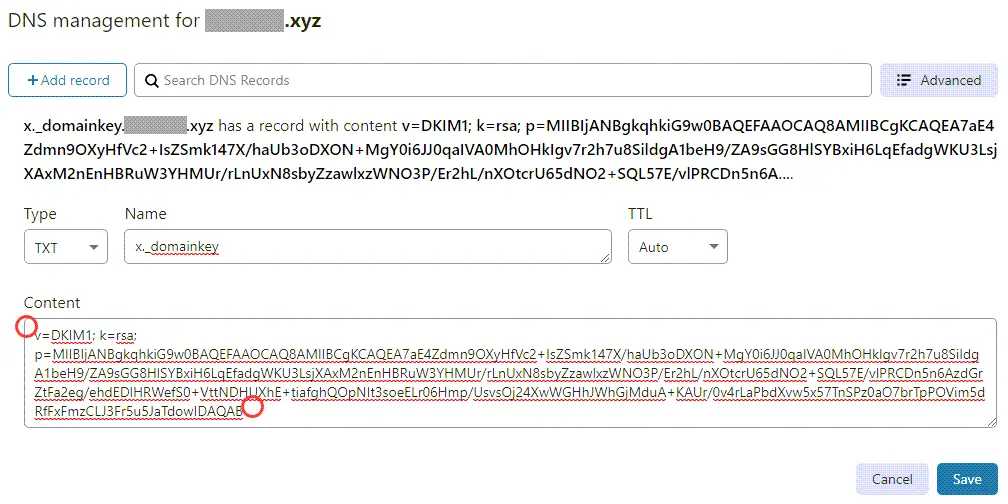

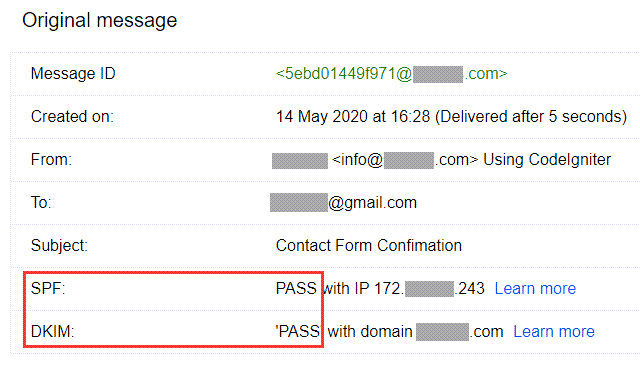
Remember to exclude double quotes “ or else dkim=fail when we check an email in Gmail > Show original
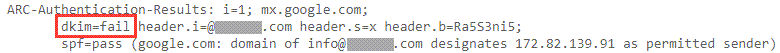
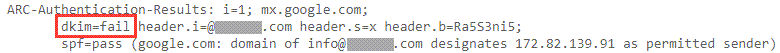
Step 2 – Add SPF (TXT) Record
The SPF record was provided via email by my email hosting provider to add as TXT record in CloudFlare DNS Management.
"v=spf1 include:mxroute.com -all"
Out of curiosity, I went to a SPF record generator spfwizard.net to verify the SPF record.
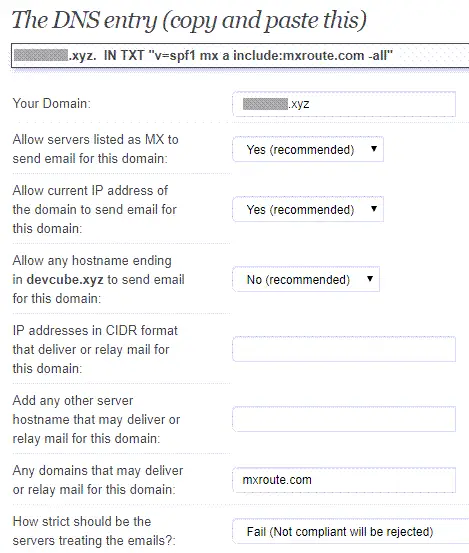

So, this is my final SPF record which differs from what my email hosting provider sent me. We will add this as TXT record to our DNS just like we add DKIM in Step 1. spf=pass with or without quotes when tested with Gmail > Show original. However, since DKIM will only pass without double quotes, we will standardize and not use them for all TXT records.
"v=spf1 mx a include:mxroute.com -all"
| In SPF record | What it means? | My opinion |
| mx | Allow servers listed as MX to send email for this domain. | MX records in DNS are purely for email purposes. If listed, I don’t see any reasons not to allow them to send email. |
| a | Allow current IP address of the domain to send email for this domain. | One of my website contact form is using PHP mail() function and other uses include send email from Linux command line with mail -s e.g. in Bash scripts or cron. Therefore, I feel is alright to allow this plus you sort of own the IP belonging to your server. |
| ipv4 | List any IP address(es) or subnet(s) authorized to deliver or relay mail for example.com | I am sending emails from my server with Postfix MTA and I had configured my email hosting provider as relayhost in /etc/postfix/main.cf hence with or without my server IP inclusion does not make any difference to dkim=pass and spf=pass. However, if you are to send emails from your server without a hosting provider, then adding this might help. Also, you should include ipv4 if you run your own email servers. |
| include | Any 3rd party domain(s) or service(s) that may deliver emails for your domain. | This is pretty standard and it depends on your mail provider. For example, Zoho – include:zoho.com Google – include:_spf.google.com Exchange – include:spf.protection.outlook.com |
| -all | How strict should be the servers treating the emails? | If you’re not going to use -all, then don’t bother with SPF at all. |
| ptr | Tests whether the DNS reverse-mapping for <ip> exists | Do not use because the PTR mechanism has been deprecated according to RFC 7208. |
Step 3 – Add MX Record
When we sign up or create a new account with an email hosting provider, we will usually receive a bunch of information via email. This includes information such as DNS MX/ TXT records, IMAP/ SMTP server, IMAP/ SMTP/ POP3 ports and Webmail login. If not, we will need to refer to their Knowledge base or User Guide to find them.
example.mxroute.com (Priority 10) example-relay.mxroute.com (Priority 20)
We will add the two MX records with different Mail server and Priority values to CloudFlare DNS Management. Some email providers, for example, Zoho provides up to three MX records mx.zoho.com, mx2.zoho.com and mx3.zoho.com
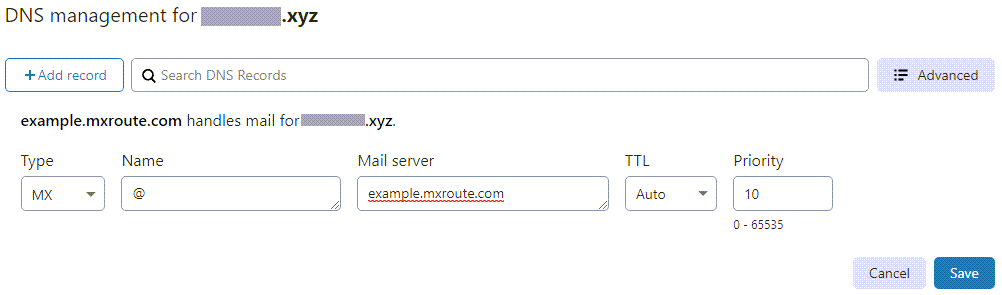

Note that these MX domains might return the same IP when we ping them because the providers want to reserve the ability to add backup relays later or room for unusual circumstances or a change in behavior.
Step 4 – PTR Record Reverse DNS Lookup
Reverse DNS resolution (rDNS) is used to determine the domain name associated to an IP address through the uses of PTR records. In my experience, both DKIM and SPF records setup are more popular but this will be added bonus to our email credibility if the PTR record is set up correctly. We can use the SolusVM management to configure the reverse DNS for our VPS.
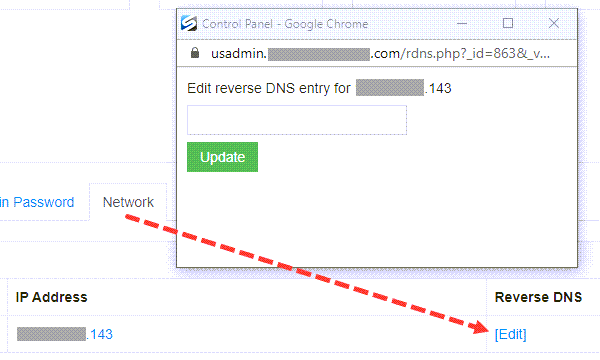

One important scenario where reverse DNS is important is when we run our own email servers because many email servers on the Internet are configured to reject incoming emails from IP addresses which does not have reverse DNS. Since we are passing our emails to the email providers server to send out on our behalf, it is more important to check that their server has a valid PTR record. We can check using Reverse Lookup tool at Mxtoolbox.
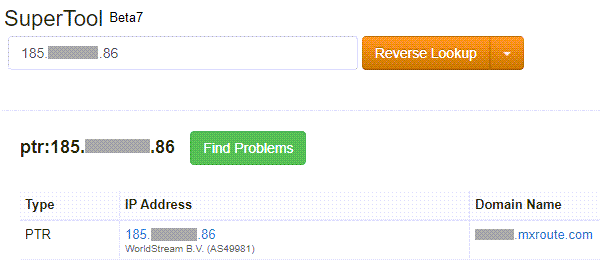

We can also use command line in Windows and Linux to perform a reverse DNS lookup.
C:\Users\Me>nslookup <ip of email hosting server>
$ dig -x <ip of email hosting server>
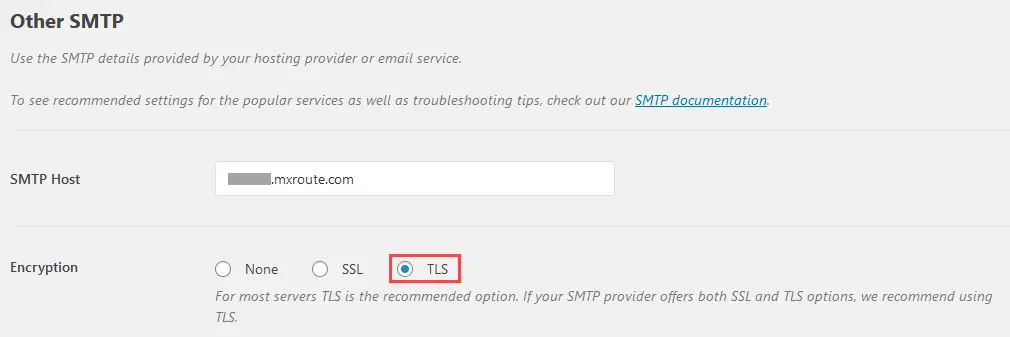
Step 5 – Using secure SMTP connections TLS
For most servers TLS is the recommended option. If your SMTP provider offers both SSL and TLS options, we should use TLS.

Conclusion
It takes very little effort to set up DKIM and SPF record to prevent email spoofing. There are numerous guides and SPF generator online and the email hosting providers documentation are very detailed if you are using popular ones like Zoho or Google. As for reverse DNS and PTR records, these are not so critical unless you are running your own email server. Besides following these technical steps to improve email delivery rates, we must also practice email etiquette. E.g. don’t use spam words and provide the opt-out option for newsletters.